Articles in this section
Communicate my IP address for scanning purposes
As part of maintaining your compliance with the Payment Card Industry Data Security Standard (PCI DSS), you may be required to conduct a scan on your network every 90 days.
How IP reporting works
These scans check your internet router to make sure that your card terminal is processing over a secure connection, reducing the risk of fraud. In order to run this scan on your behalf, your payment provider will need your public IP address. This is a series of numbers and dots that is in effect, your address on the internet.
Without this address, they will be unable to ensure that they are running the scan on the correct network.
By checking the box under the ‘Settings‘ tab, your payment provider will be able to run these scans on your behalf without the need to call you to confirm the IP address every time.
This feature is only effective if this device is permanently located at your primary address and connected to the same internet connection as your card payment terminal. If you are unsure whether this is necessary, speak to your payment provider for more information.
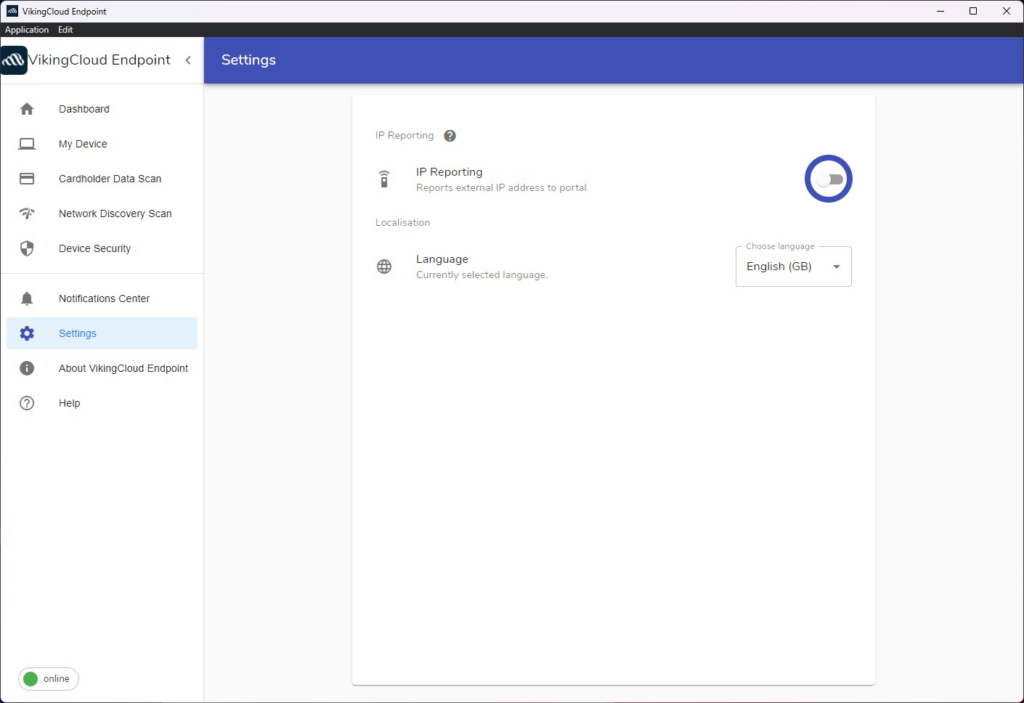
Click the checkbox to turn on IP Reporting.
Top articles
These are the steps to download VikingCloud Protect to your Windows device.
Read MoreCheck your device for any files that may contain un-encrypted full credit card numbers.
Read MoreExamine your device’s security configuration for common vulnerabilities.
Read More